2020 – IV Quarterly Bulletin
NC3 TOP – Threat Observatory Platform
Threat Agent activities
Behind every cyber-attack there is an actor with a specific intent. However, for many events, the identity and general motivation are unknown. On the other hand, some groups have been well known for years and their criminal activities and techniques are documented and monitored. Typically, they conduct targeted attacks against specific organisations, using relatively sophisticated tools and attack procedures.
Some of them are considered as State-sponsored, but the actual link with various countries stays often subject of controversies and should be considered with prudence.
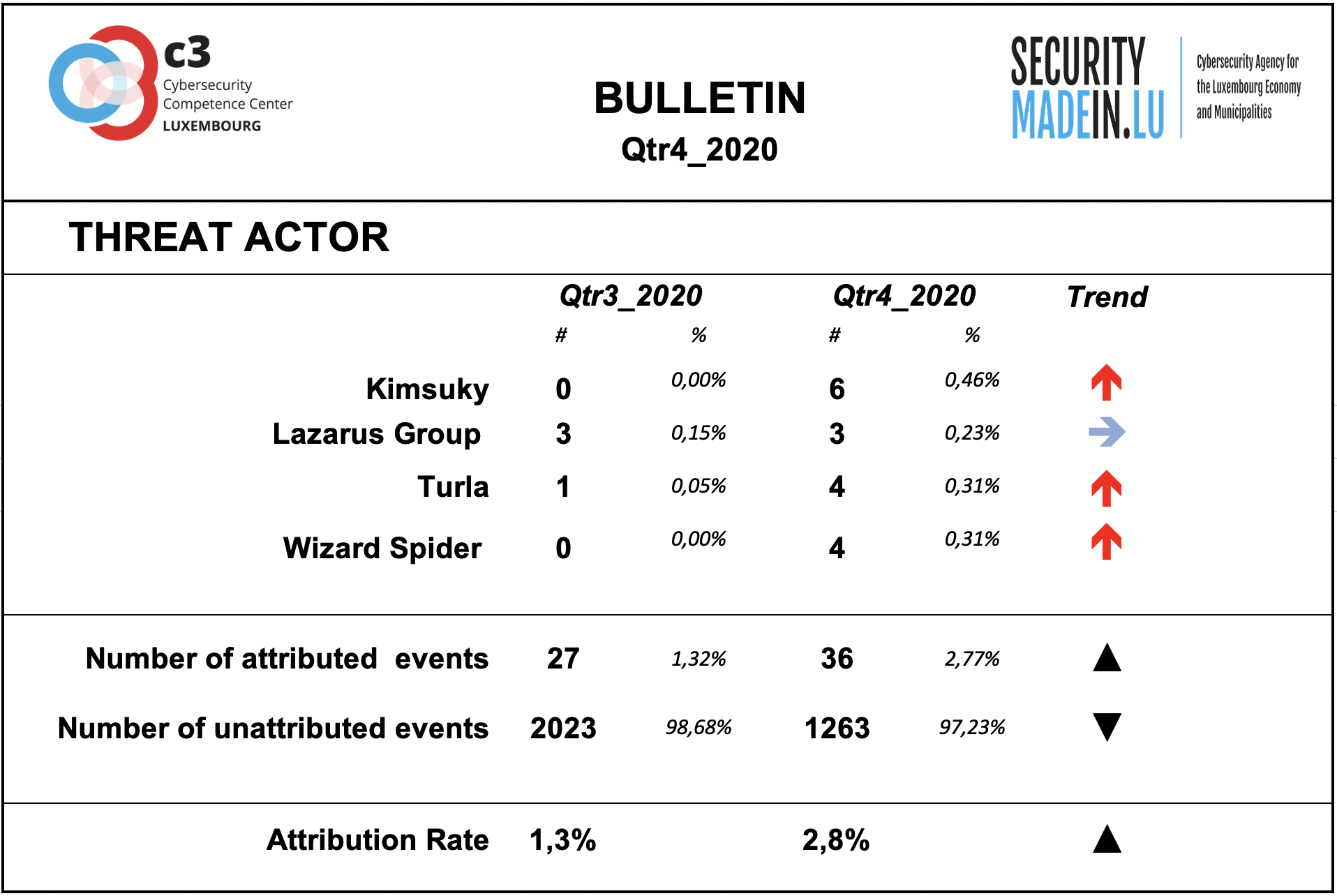
During the fourth quarter of 2020 has been observed an increase of identifiable threat groups’ activity. Comparing the fourth quarter of 2020 with third quarter of 2020, the increase can be estimate around +33 %.
As during previous quarters, the attribution rate of events is very low. This means that most of the ongoing attacks are not attributable.
According to the attribution found in the MISP records, the following groups were particularly active during this quarter:
Kimsuky North Korea-based cyber espionage group that has been active since at least 2012. The group initially focused on targeting South Korean government entities, think tanks, and individuals identified as experts in various fields, and expanded its operations to include the United States, Russia, Europe, and the UN. Kimsuky has focused its intelligence collection activities on foreign policy and national security issues related to the Korean peninsula, nuclear policy, and sanctions
Lazarus group is a North Korean state-sponsored cyber threat group; it uses a wide range of methods depending on the characteristics of the campaigns carried out and the objectives pursued. It mainly aimed at manipulating employees of strategically important companies such as those involved in the military or aerospace industry;
Turla is a Russian-based threat group specialised in espionage activities and intelligence gathering motivations, targeting organizations worldwide. It is suspected to be sponsered by Russian state; Turla’s espionage platform is mainly used against Windows machines, but has also been seen used against macOS and Linux machines.
Wizard Spider is the Russia-based operator of the TrickBot banking Trojan that targets both businesses and consumers for their data, such as banking information, account credentials, personally identifiable information and even bitcoins. As a highly modular malware, it can adapt to many environments or network.
External transfer pathway and infrastructures
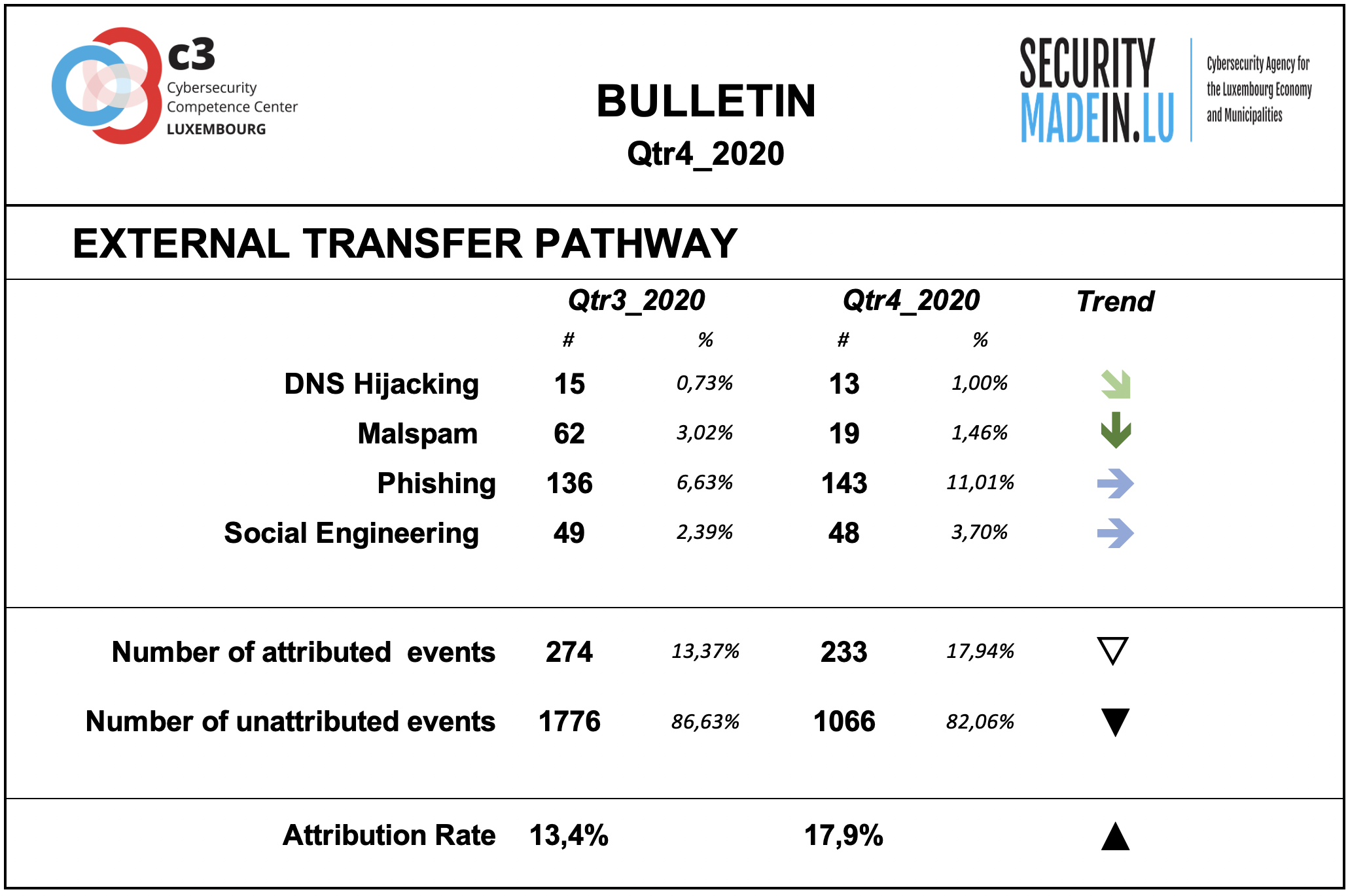
The transfer of the malicious artefacts or payloads is done through a number of different types of technical procedures and infrastructures.
The records related to this period confirmed that the most frequently used strategy is associated with scams that use email or similar approaches to reach potential victims.
Phishing is the most common strategy. In most of these cases, the pathway is a human to human or machine to human infrastructure.
This period generally confirms the figures of the previous period, with the exception of malspam events, i.e., spam email that delivers malware, that decrease.
The attribution rates are significantly better than for threat actors, even if still fairly low. Attribution means that it was possible to identify the external transfer pathway for a given event.
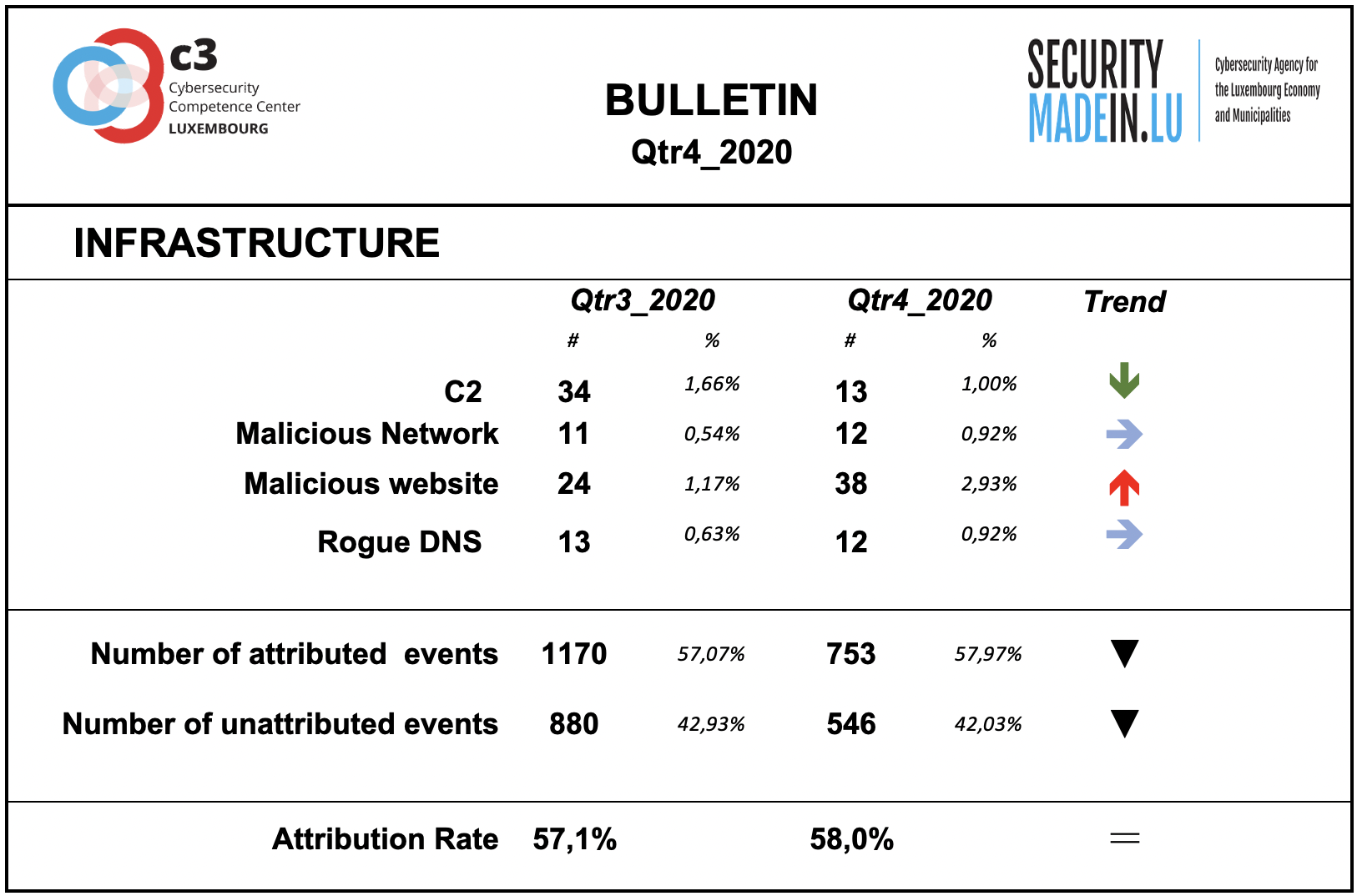
Infrastructures represent the type of systems being used for supporting attacks. Some are meant to compromise or help compromise, the targeted system, others are more focused on helping to maintain the foothold in it. Indeed, once access to a system device has been gained, a communication channel is maintained through the use of command and control (C2) infrastructures. The specific mechanisms vary greatly between attacks, but C2 generally consists of one or more covert communication channels between devices in a victim organization and a platform that the attacker controls. These communication channels are supporting the malicious activities. They are used to issue instructions to the compromised devices, download additional malicious payloads, and pipe stolen data back to the cyber-actor.
During this period, there was a clear decrease in the use of C2 infrastructures and an increase of the use of malicious websites.
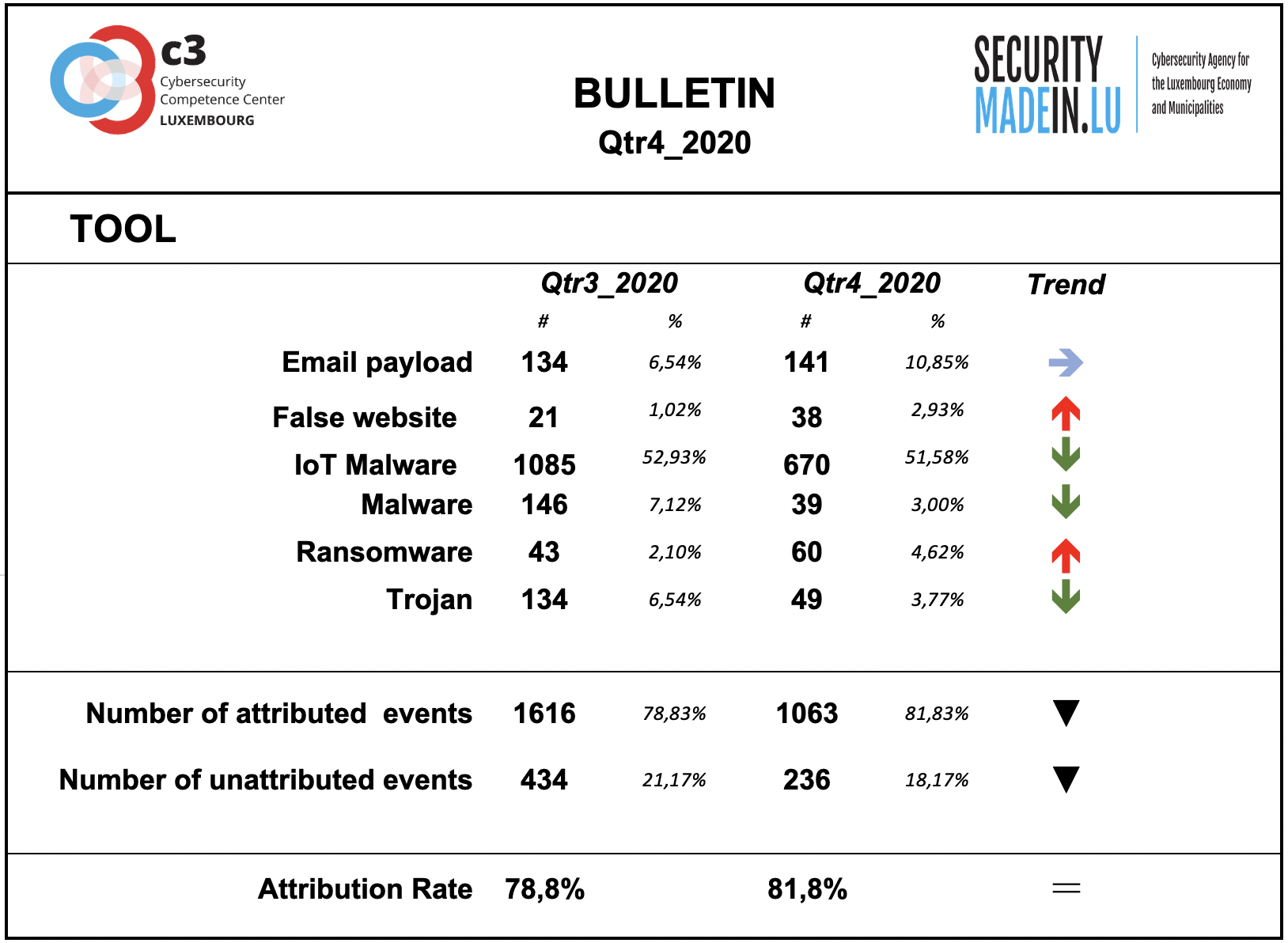
Tool
The monitoring system showed a substantial prevalence of the use of malware although a significant decrease was noted compared to the previous period. It also recorded an increase in the use of false websites and Ramsomware.
Compared to the other dimensions of the interpretation model, this dimension is confirmed as having the highest attribution rate.
Points of access
The most common access point reported by MISPPRIV users is e-mail, which isn’t too surprising as it’s an effective ingress vector for several types of attacks. It’s often exploiting users’ weaknesses, be they voluntary (negligence) or involuntary lack of knowledge about a specific threat.
However, it’s important to keep in mind that the attribution rate is rather low. Most of the attacks’ point of access is not known.
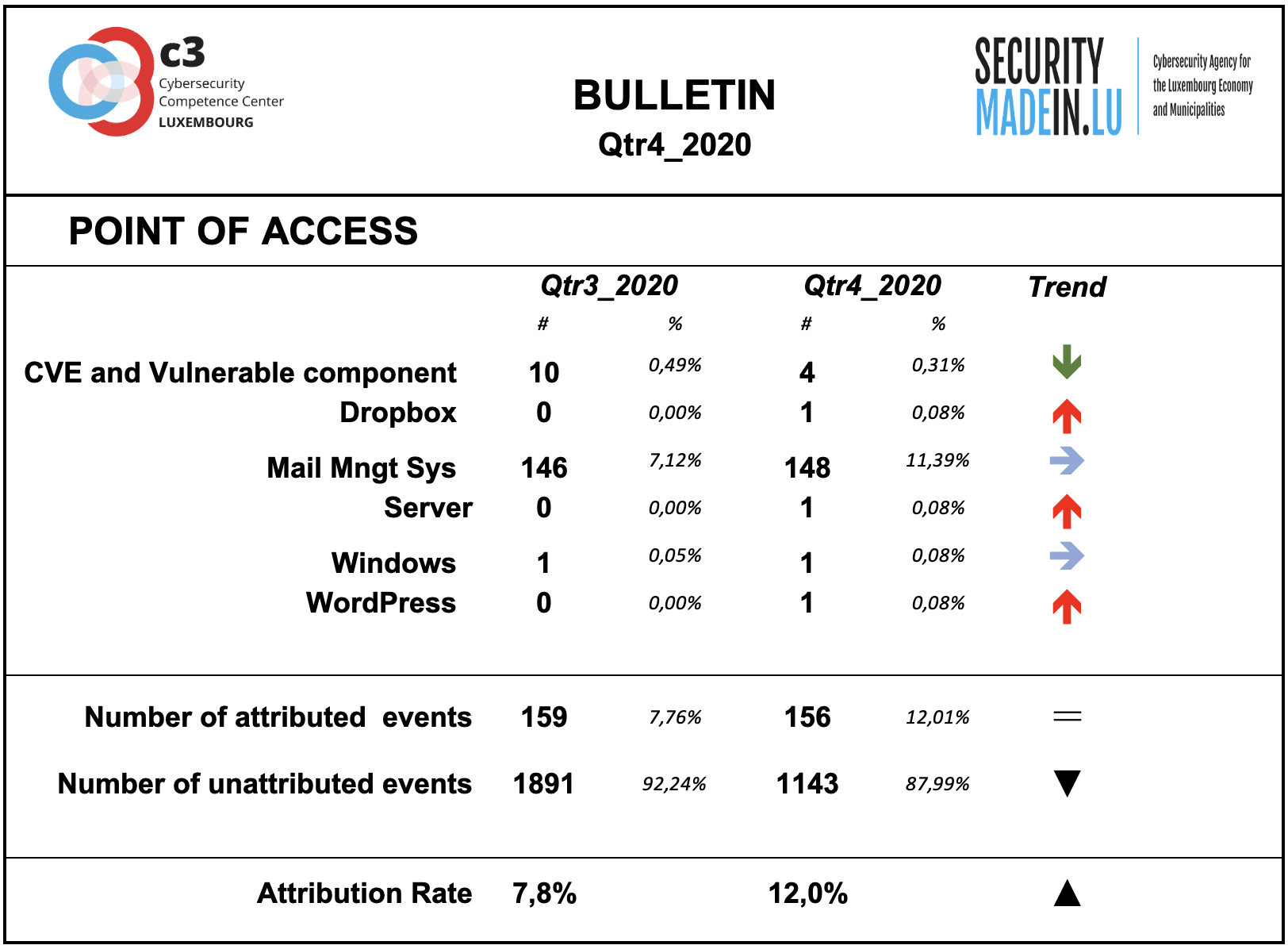
With regard to component and system vulnerabilities, the monitoring system identified the following:
A SolarWinds Orion API is vulnerable to an authentication bypass; successful attacks of this vulnerability can result in takeover of Oracle WebLogic Server;
NETGEAR JGS516PE devices before 2.6.0.43 are affected by lack of access control;
Number of vulnerabilities associated to Microsoft Exchange server;
Several vulnerabilities related to VMware vCenter Server;
Several vulnerabilities related to Polaris kernel of Cisco Catalyst;
Several vulnerabilities related to Pulse Connect Secure;
Vulnerability in the Oracle WebLogic Server.
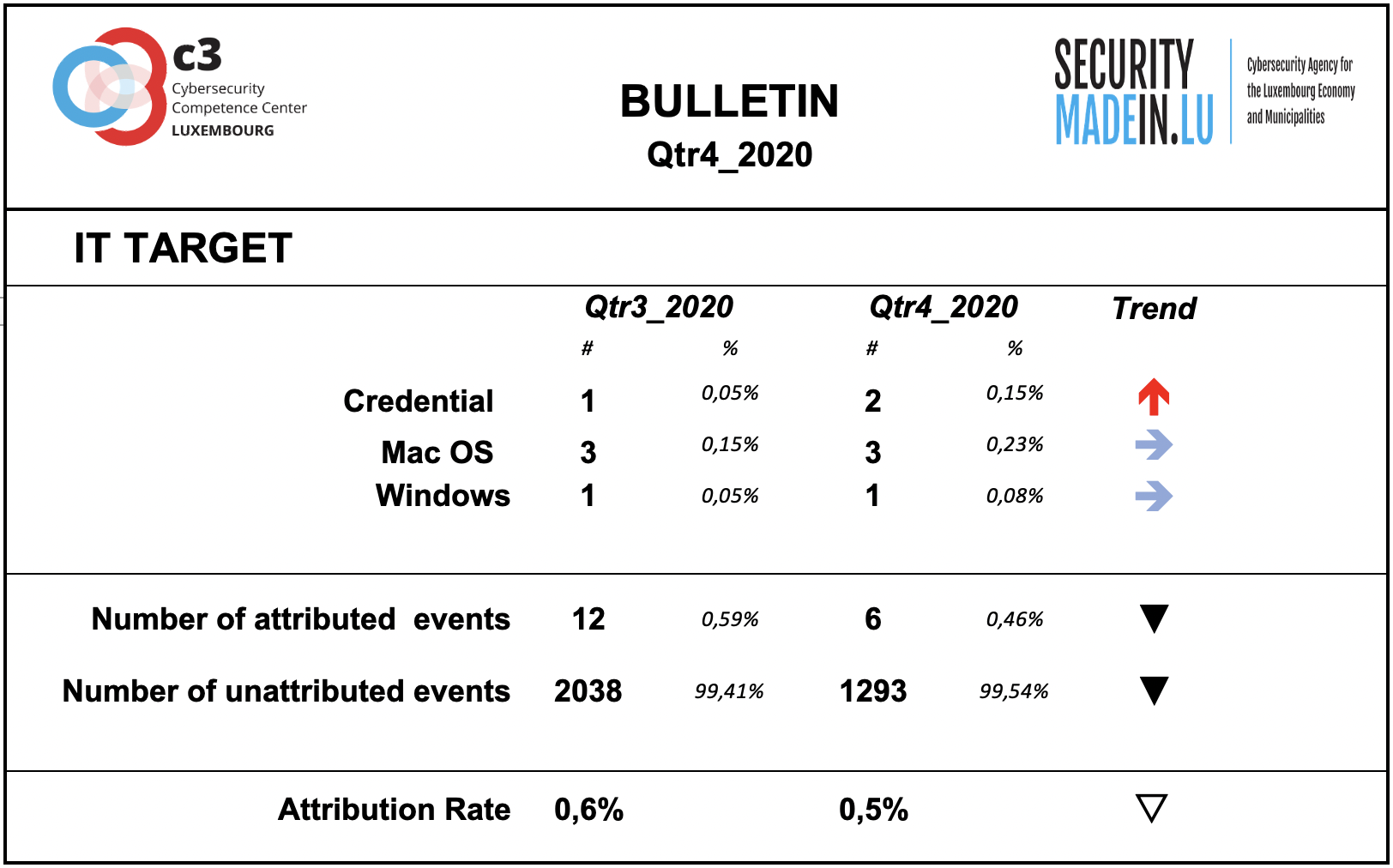
IT Target
Information on the attacked IT target is not sufficiently described by the analysed events.
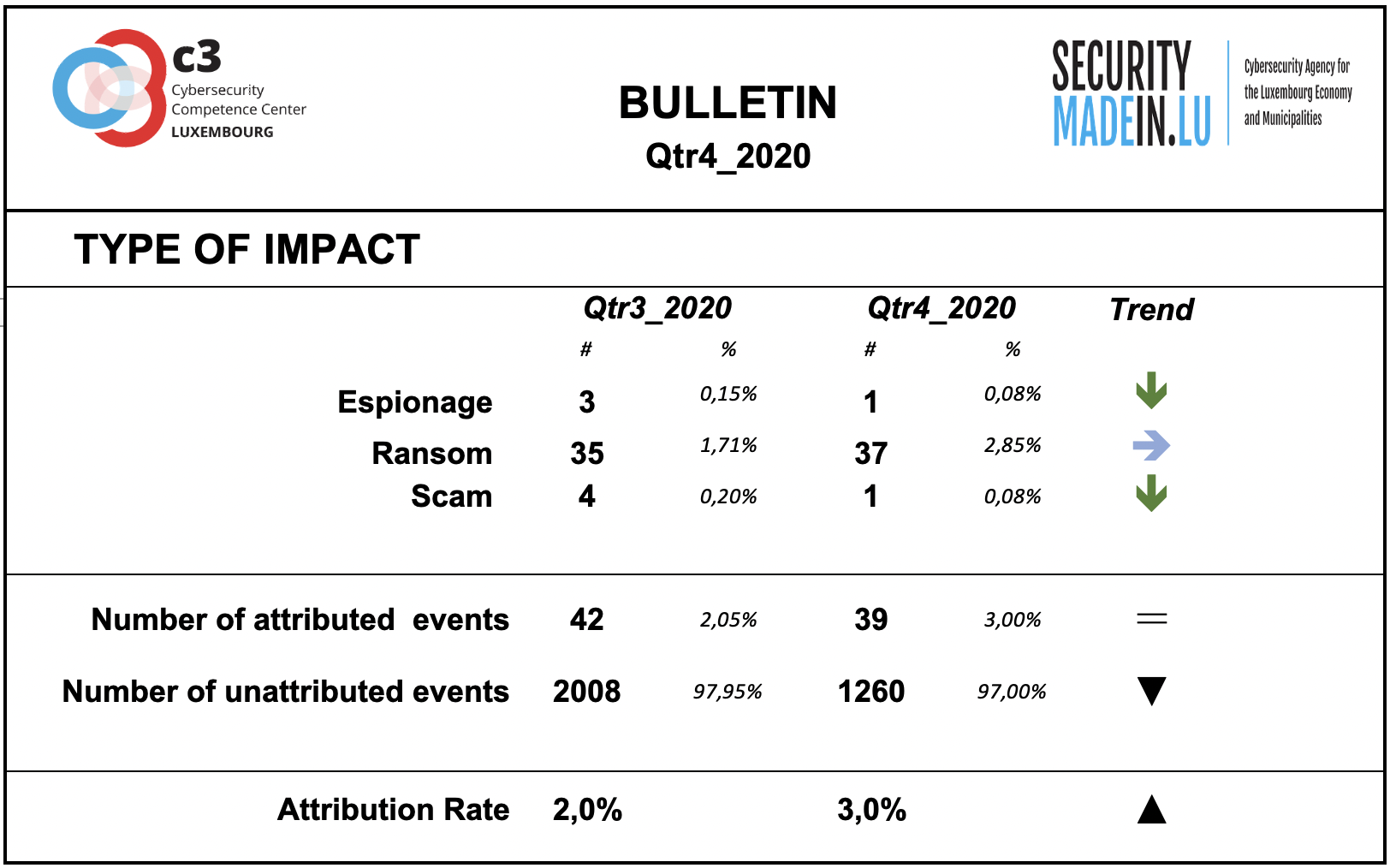
Type of Impact
The attribution rate for this dimension is very low and not sufficiently described.
Information on the type of consequences for the victim is mainly related to ransom demands, which remain constant compared to the previous period.
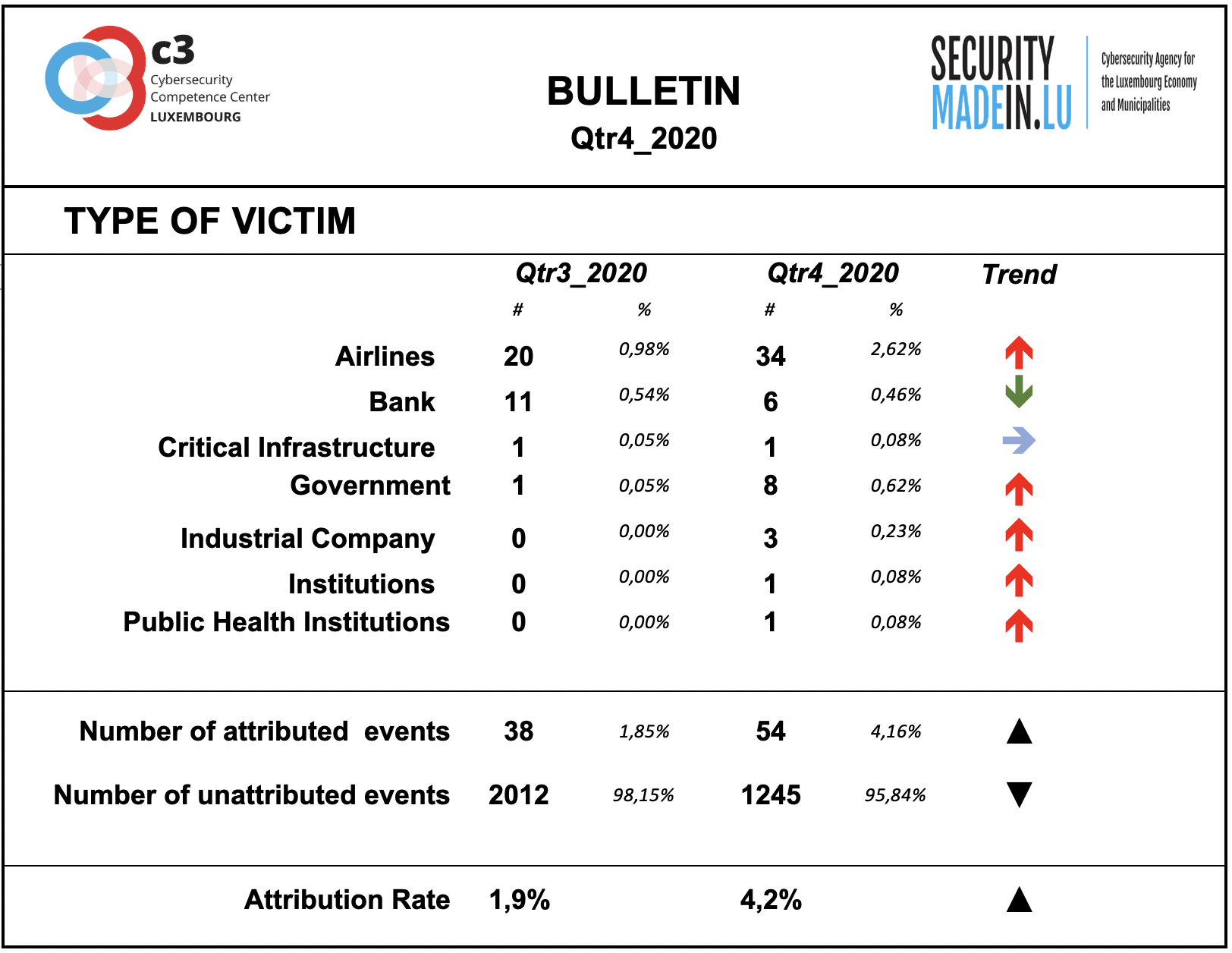
Type of Victim
During this period there has been an increase of attacks on airlines, Governments and industrial companies.