2021 - Annual Bulletin
NC3 TOP – Threat Observatory Platform
Threat Agent activities
Behind every cyber-attack there is an actor with a specific intent. However, for many events, the identity and general motivation are unknown. On the other hand, some groups have been well known for years and their criminal activities and techniques are documented and monitored. Typically, they conduct targeted attacks against specific organisations, using relatively sophisticated tools and attack procedures.
Some of them are considered as State-sponsored, but the actual link with various countries stays often subject of controversies and should be considered with prudence.
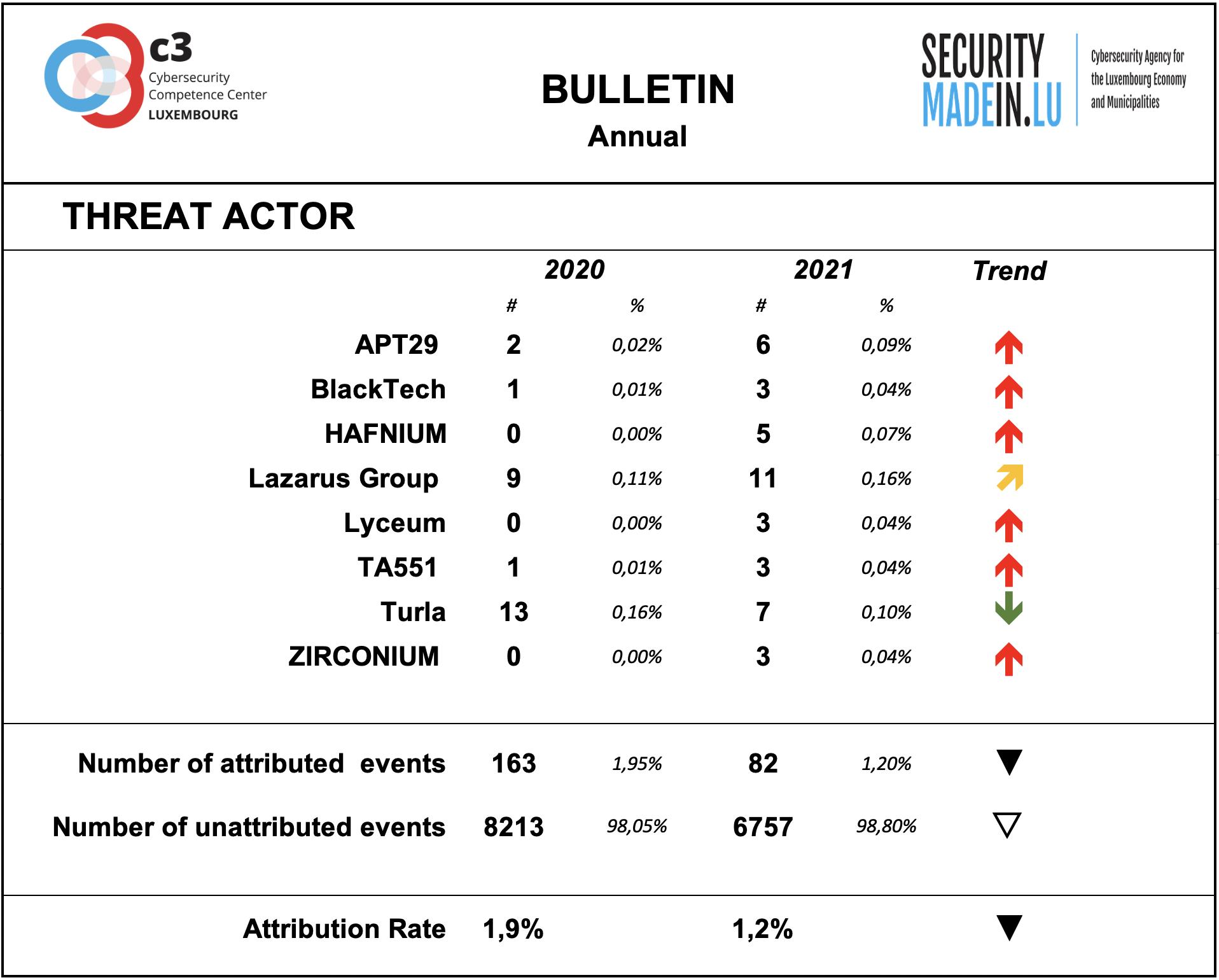
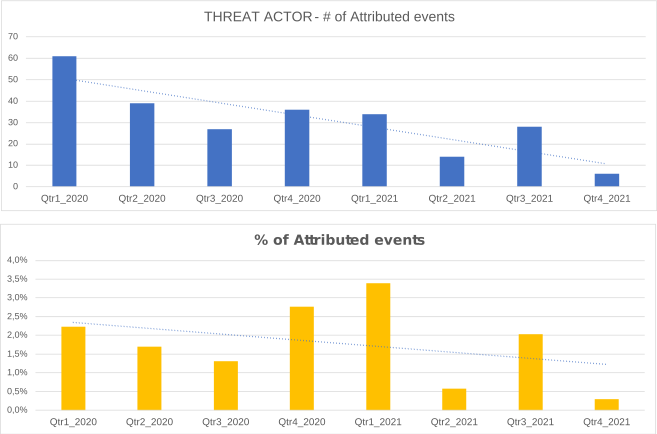
During 2021, a significant decrease in the activity of the identifiable threat groups was observed, estimated at a decrease in the order of 50 % compared to the previous year.
As during previous year, the attribution rate of events is very low. This means that most of the ongoing attacks are not attributable.
During the first quarter, a new malware group, codenamed Hafnium, emerged and it massively targeted Microsoft Exchange servers. Attacks caused major impacts and disruptions worldwide. The exploitation of Microsoft Exchange allowed HAFNIUM to install web shells for persistent access to systems and then to move laterally, using compromised credentials to authenticate.
During December 2021, a variety of groups, including some state-sponsored, exploited Log4Shell vulnerabilities as an access vector to enable ransomware operations and other criminal activities.
According to the attribution found in the MISP records, the following groups were particularly active during the year:
APT29 is a Russian hacker group believed to be associated with one or more intelligence agencies of Russia; it primarily targets Western governments and related organizations, such as government ministries and agencies, political think tanks, and governmental subcontractors;
BlackTech is a cyber espionage group operating against targets in East Asia, particularly Taiwan, and occasionally, Japan and Hong Kong. Based on the mutexes and domain names, BlackTech’s campaigns are likely designed to steal their target’s technology;
HAFNIUM: this group is apparently operating from China. As documented by several security or IT organisations including Microsoft, it conducted a mass attack on Microsoft's Exchange software, which allowed to take control of many corporate servers, stealing e-mails, calendars, and any other sensitive information. The mass attack started in late February and early March. Thousands of companies fell victim. Many more were affected in the days following Microsoft's distribution of an emergency patch due to companies not updating their systems in time. The campaign was identified as a potential espionage mission due to the nature of the information stolen. Hafnium is believed to be affiliated with the Chinese State;
Lazarus group is a North Korean state-sponsored cyber threat group; it uses a wide range of methods depending on the characteristics of the campaigns carried out and the objectives pursued. It mainly aimed at manipulating employees of strategically important companies such as those involved in the military or aerospace industry;
Lyceum is an emerging threat to energy organizations in the Middle East, but it should not assume that future targeting will be limited to this sector. Lyceum 's targeting of telecommunications has been speculated to be part of an effort to establish man-in-the-middle capabilities throughout the Middle East region;
TA551 is a financially-motivated threat group that has been active since at least 2018. The group has primarily targeted English, German, Italian, and Japanese speakers through email-based malware distribution campaigns;
Turla is a Russian-based threat group specialised in espionage activities and intelligence gathering motivations, targeting organizations worldwide. It is suspected to be sponsered by Russian state; Turla’s espionage platform is mainly used against Windows machines, but has also been seen used against macOS and Linux machines;
ZIRCONIUM is a threat group operating out of China, active since at least 2017, that has targeted individuals associated with the 2020 US presidential election and prominent leaders in the international affairs community.
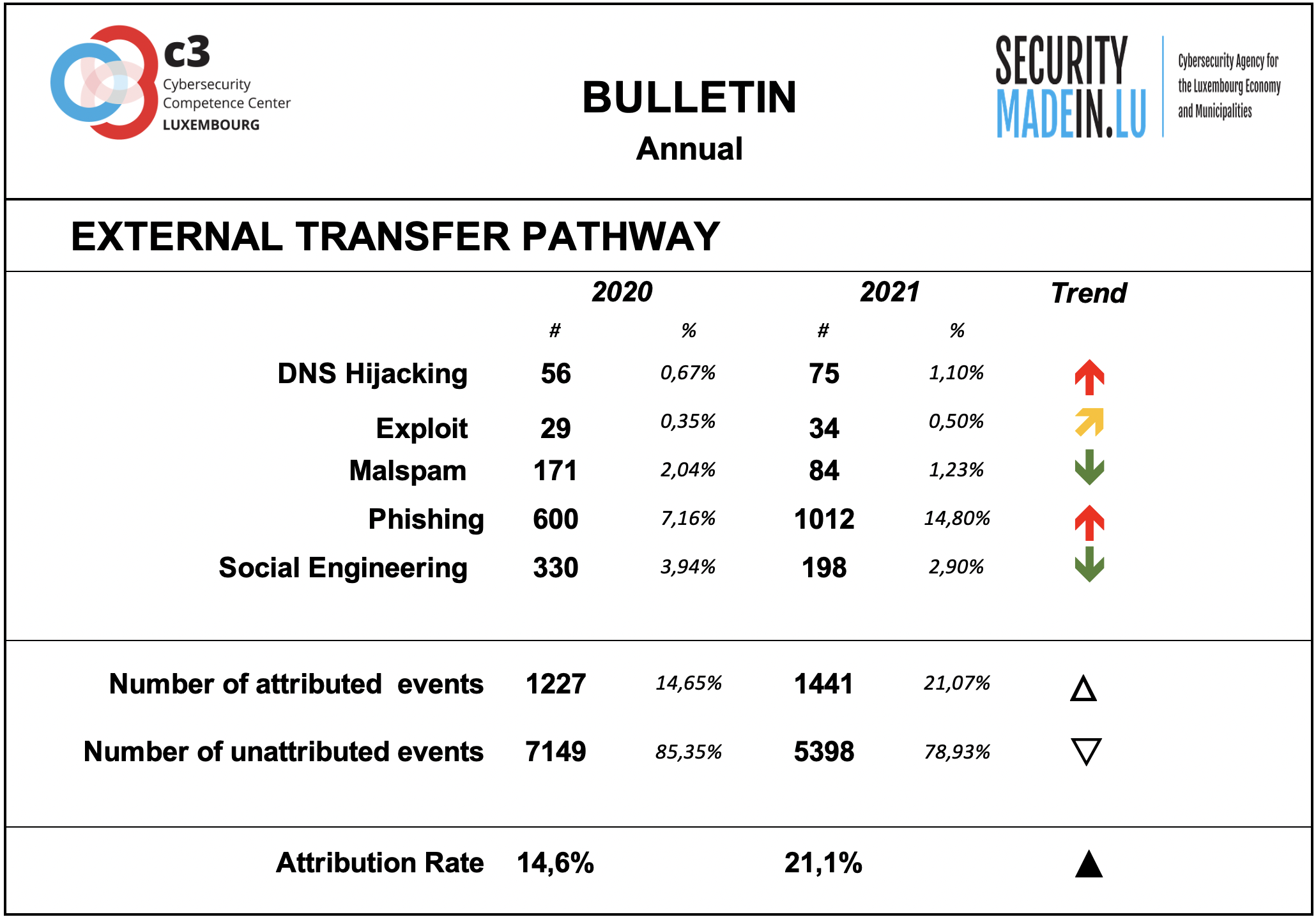
External transfer pathway and infrastructures
The transfer of the malicious artefacts or payloads is done through a number of different types of technical procedures and infrastructures.
Also, during 2021, it was confirmed that the most frequently used strategy is associated with scams that use email or similar approaches to reach potential victims.
Phishing is the most common strategy, but there has also been an increase in malspam and smishing events. In most of these cases, the pathway is a human to human or machine to human infrastructure.
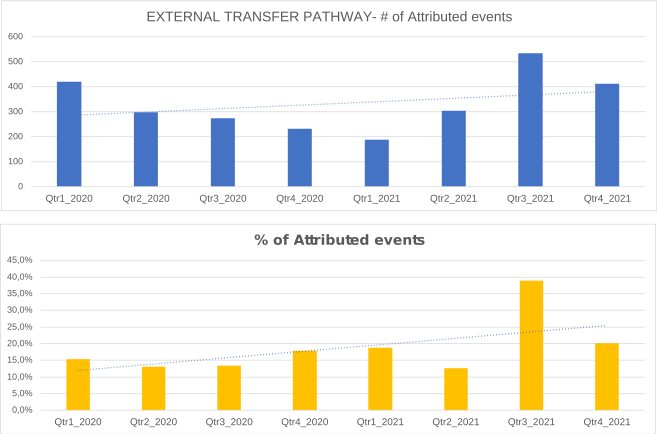
Recorded phishing events recorded by the monitoring system have increased significantly over 2021, with an increase of about 69 %.
During 2021, the monitoring system recorded an increase in Domain Name Server (DNS) hijacking. DNS hijacking is a type of attack in which DNS queries are incorrectly resolved in order to unexpectedly redirect users to malicious sites. To carry out the attack, the perpetrators install malware on users' computers, take control of routers, or intercept or violate DNS communication.
DNS hijacking can be used for pharming (in this context, attackers typically display unwanted ads to generate revenue) or phishing (displaying fake versions of sites users access and stealing data or credentials).
The attribution rates are significantly better than for threat actors, even if still fairly low. Attribution means that it was possible to identify the external transfer pathway for a given event.
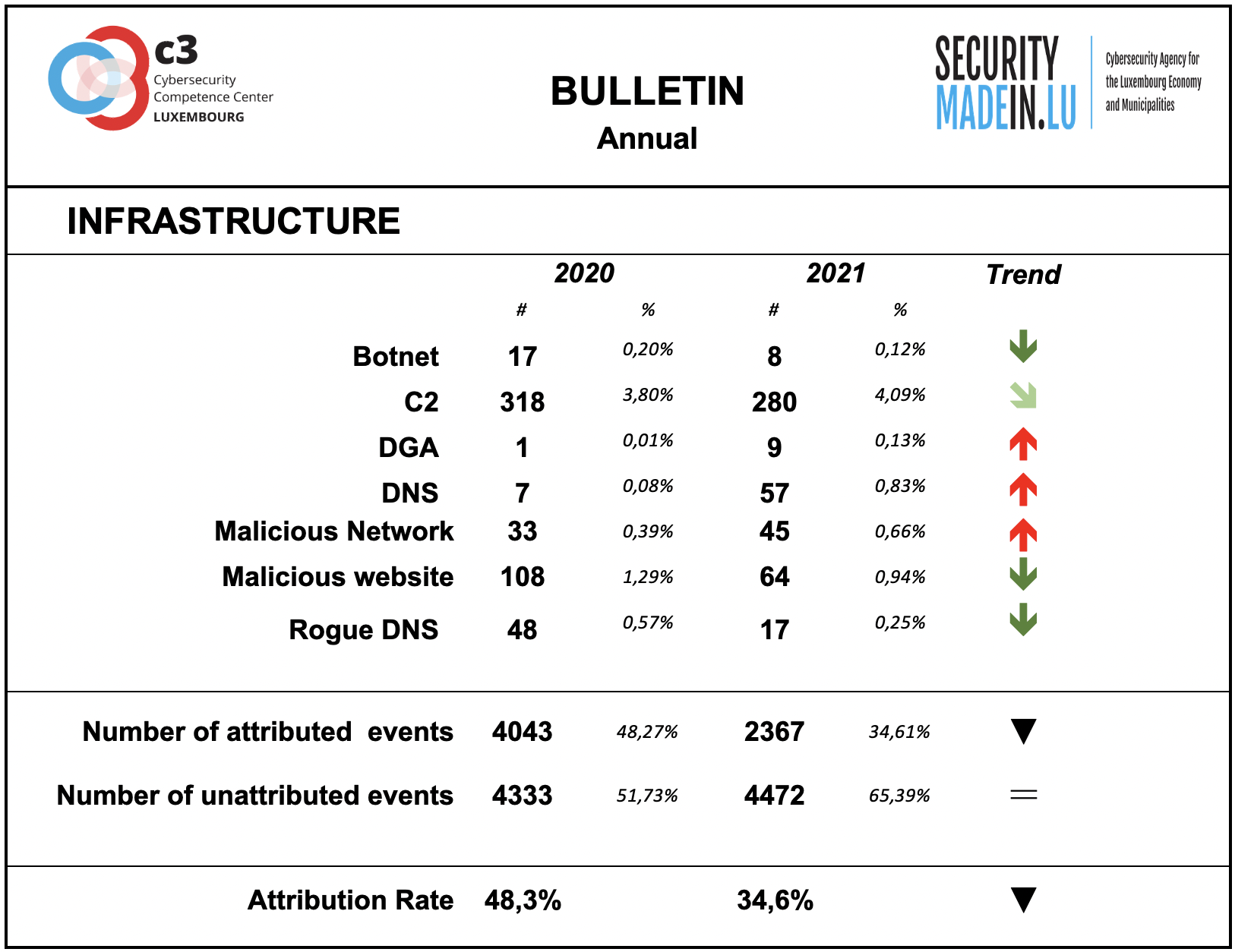
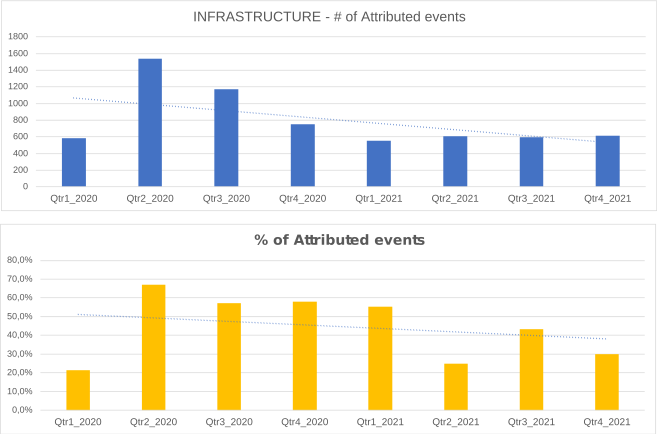
Infrastructures represent the type of systems being used for supporting attacks. Some are meant to compromise or help compromise, the targeted system, others are more focused on helping to maintain the foothold in it. Indeed, once access to a system device has been gained, a communication channel is maintained through the use of command and control (C2) infrastructures. The specific mechanisms vary greatly between attacks, but C2 generally consists of one or more covert communication channels between devices in a victim organization and a platform that the attacker controls. These communication channels are supporting the malicious activities. They are used to issue instructions to the compromised devices, download additional malicious payloads, and pipe stolen data back to the cyber-actor.
The monitoring system revealed an increase in the number of cases of DGA (Domain Generation Algorithms) and the use of malicious networks.
On the contrary, it recorded a significant decrease in the use of IoT and malicious websites.
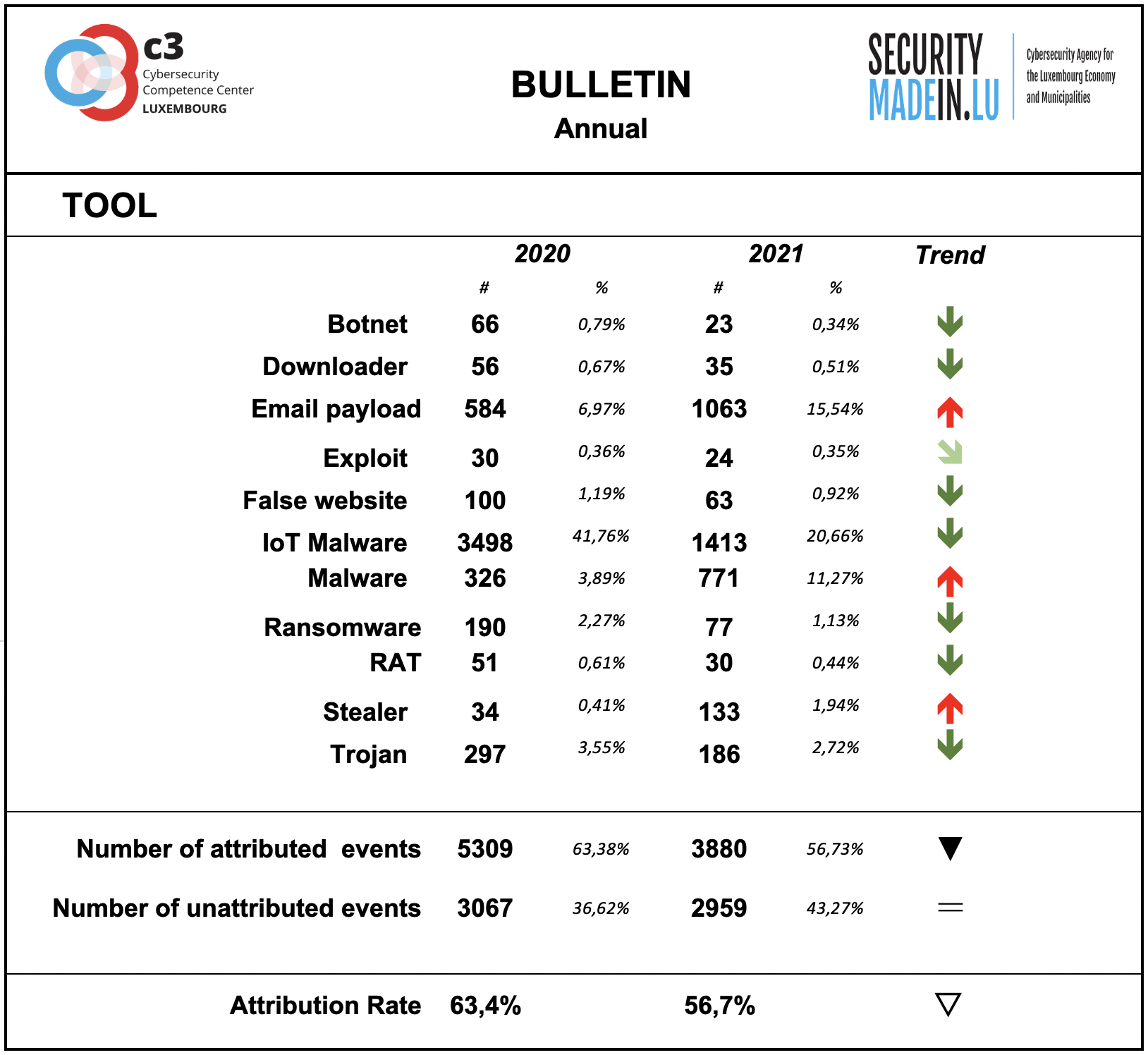
Tool
The monitoring system showed a substantial prevalence of the use of Malware especially associated with IoT systems.
During 2021, there was a significant increase (+ 136% increase) in events using malware and in delivery of payloads by email (+82% increase).
It should also be highlighted a significant increase in stealers of credentials and environmental information.
In contrast, the monitoring system recorded a decrease in the number of ransomware attacks along with the use of Trojan tools.
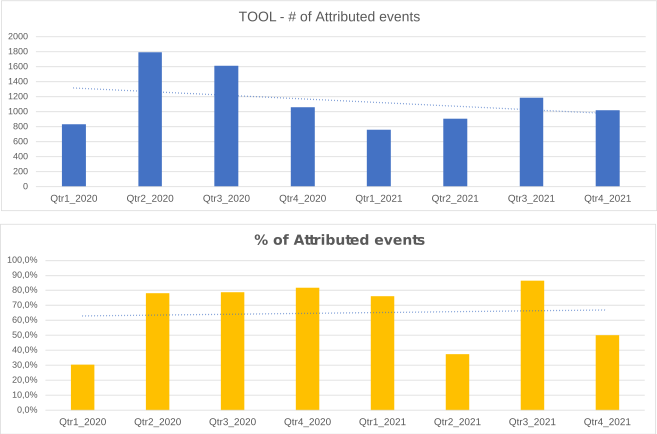
Compared to the other dimensions of the interpretation model, this dimension is confirmed as having the highest attribution rate.
Points of access
The most common access point reported by monitoring system is e-mail, which isn’t too surprising as it’s an effective ingress vector for several types of attacks. It’s often exploiting users’ weaknesses, be they voluntary (negligence) or involuntary (lack of knowledge about a specific threat.
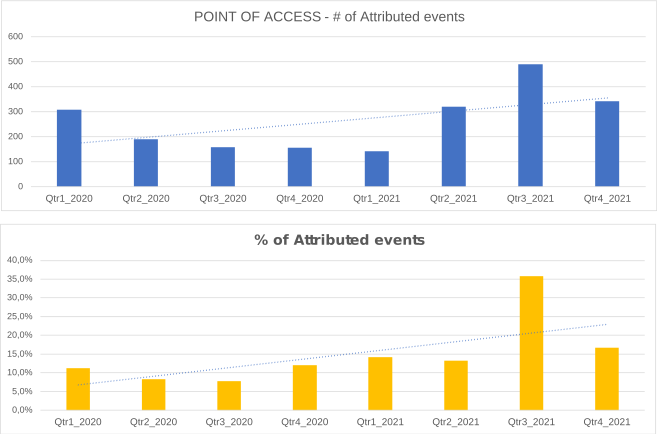
As already highlighted in previous chapters, phishing activities have increased significantly. However, it’s important to keep in mind that the attribution rate is rather low. Most of the attacks’ point of access is not known.
In any case, it should be noted that a number of high-profile vulnerabilities were exploited during 2021. Of these, the vulnerabilities associated with the following systems should be noted for the number of endpoints potentially affected:
A series of vulnerabilities in Microsoft Exchange - now collectively known as ProxyLogon and ProxyShell - characterised the massive attacks recorded during the first few months of the year, although they continued for the remainder of the year. Microsoft Exchange vulnerabilities were predominantly used to attack numerous organisations worldwide. Attackers have mainly developed techniques to collect credential information and to secure a durable entry point into the victim's environment and to then move laterally.
A vulnerability reported in November 2021 related to Apache's Log4j2, a logging library used by many web applications, was exploited for a series of attacks by injecting arbitrary Java code into web services. Specially crafted requests allowed access to private systems and the delivery of malware or the acquisition of sensitive data such as user credentials; The Log4j2 log library is used by many systems and is widely used. It is, therefore, very difficult to predict which products are vulnerable. The exploitation of this vulnerability is expected to continue in 2022 even though a mitigation strategy has already been defined and an updated version of the library has been released.
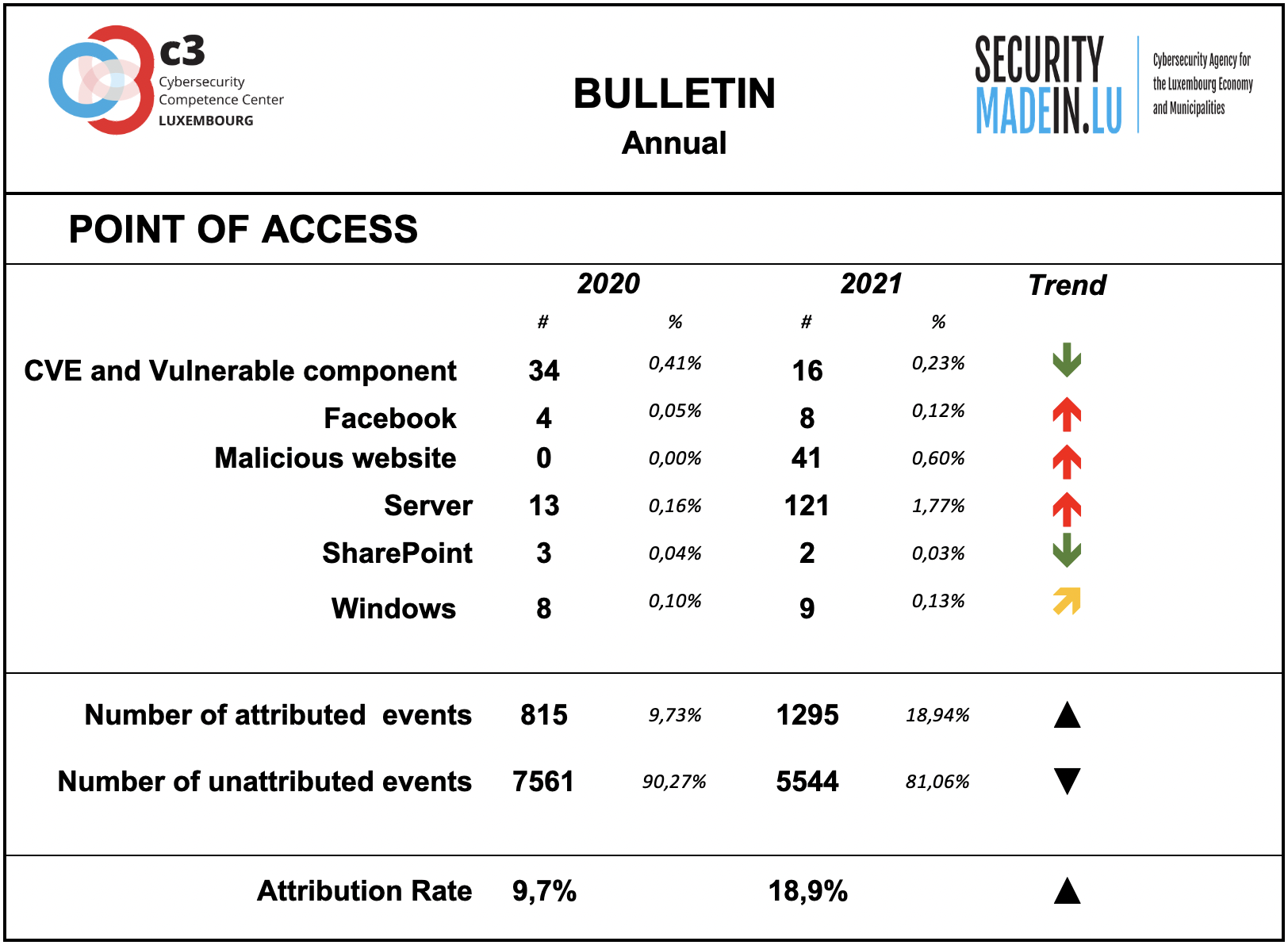
With regard to component and system vulnerabilities, the monitoring system identified the following:
A vulnerability in the Firewall SonicWall Email Security version 10.0.9.x allows an attacker to create an administrative account;
A vulnerability of Micro Focus Operation Bridge Reporter (OBR) product, allows Remote Code Execution;
Accellion FTA (File Transfer Appliance)
BQE BillQuick Web Suite has vulnerabilities that allow SQL injection remote command execution;
Buffalo WSR-2533DHPL2 firmware - authentication vulnerability;
Cisco Nexus 9000 Series Fabric Switches in Application Centric Infrastructure (ACI) Mode could allow the generation of DoS type of attack.
ForgeRock AM server - deserialisation vulnerability;
GitLab has vulnerabilities that allow remote command execution;
Kaseya VSA allows credential disclosure;
McAfee Total Protection (MTP)
Number of vulnerabilities associated to Microsoft Exchange;
Pulse Connect Secure has vulnerable to an authentication process and to execute arbitrary code;
Realtek SDK: there are several remotely exploitable vulnerabilities; a Realtek SDK is used in IoT devices sold by a long list of manufacturers that can enable an attacker to gain complete control over an affected device. The flaws affect many popular devices such as IP cameras, routers, WiFi repeaters, and others from manufacturers including Buffalo, ASUS, Belkin, D-Link, LG, Logitec, and Realtek itself.
Router Tenda AC11;
Several vulnerabilities in Acrobat Reader, iOS, Google Chrome, Windows, Google Chrome, Microsoft Exchange
SolarWinds allows a remote code execution;
the router D-Link DIR-825
Trend Micro Apex One has a improper input validation vulnerability in
vSphere Client (HTML5) contains several remote code execution vulnerabilities;
Yealink Device Management has vulnerabilities that allow command injection;
- Zoho ManageEngine is vulnerable to REST API authentication bypass;
It is extremely important to highlight that some events exploited vulnerabilities already identified in 2020:
Vulnerability of the Router D-Link DNS-320 FW;
Vulnerability of the Router D-Link DIR-825 R1;
Vulnerability of Google Chrome
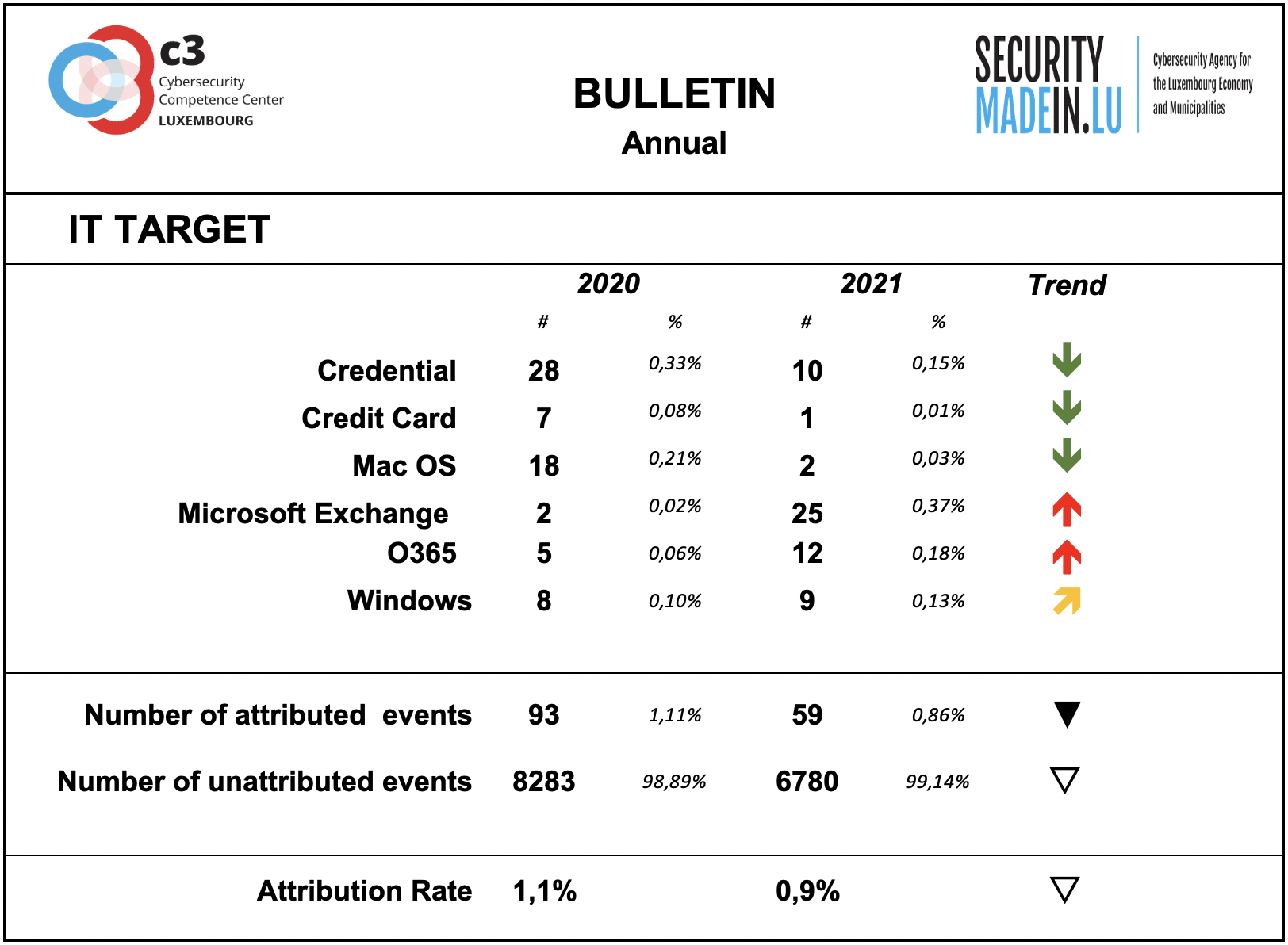
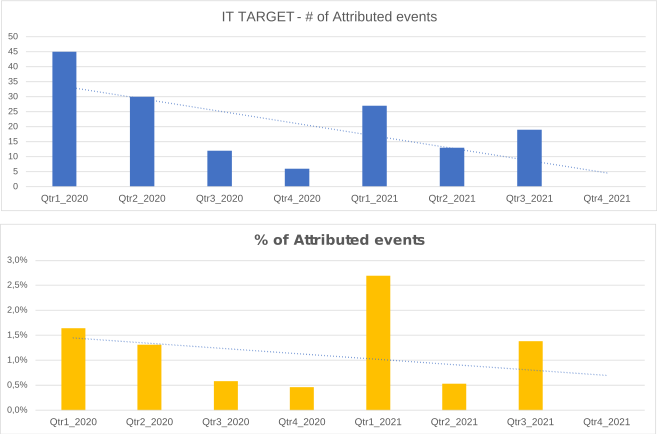
IT Target
Information on the attacked IT target is not sufficiently described by the analysed events.
Type of Impact
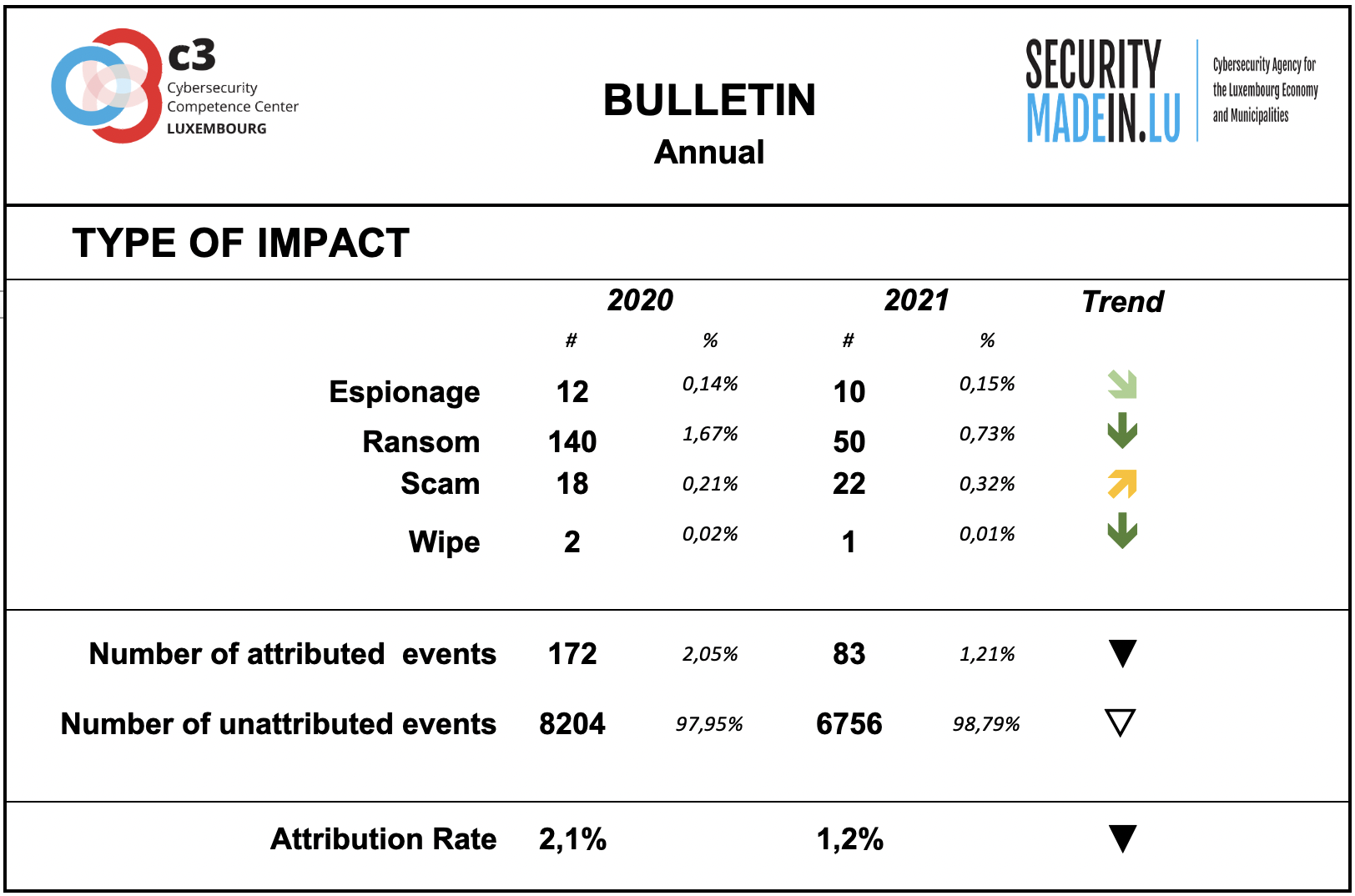
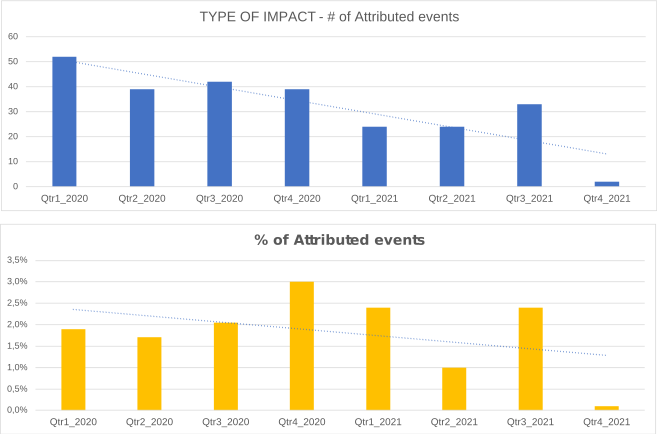
Information on the type of consequences for the victim is mainly related to ransom demands, although fewer events were recorded in 2021 than in the previous year.
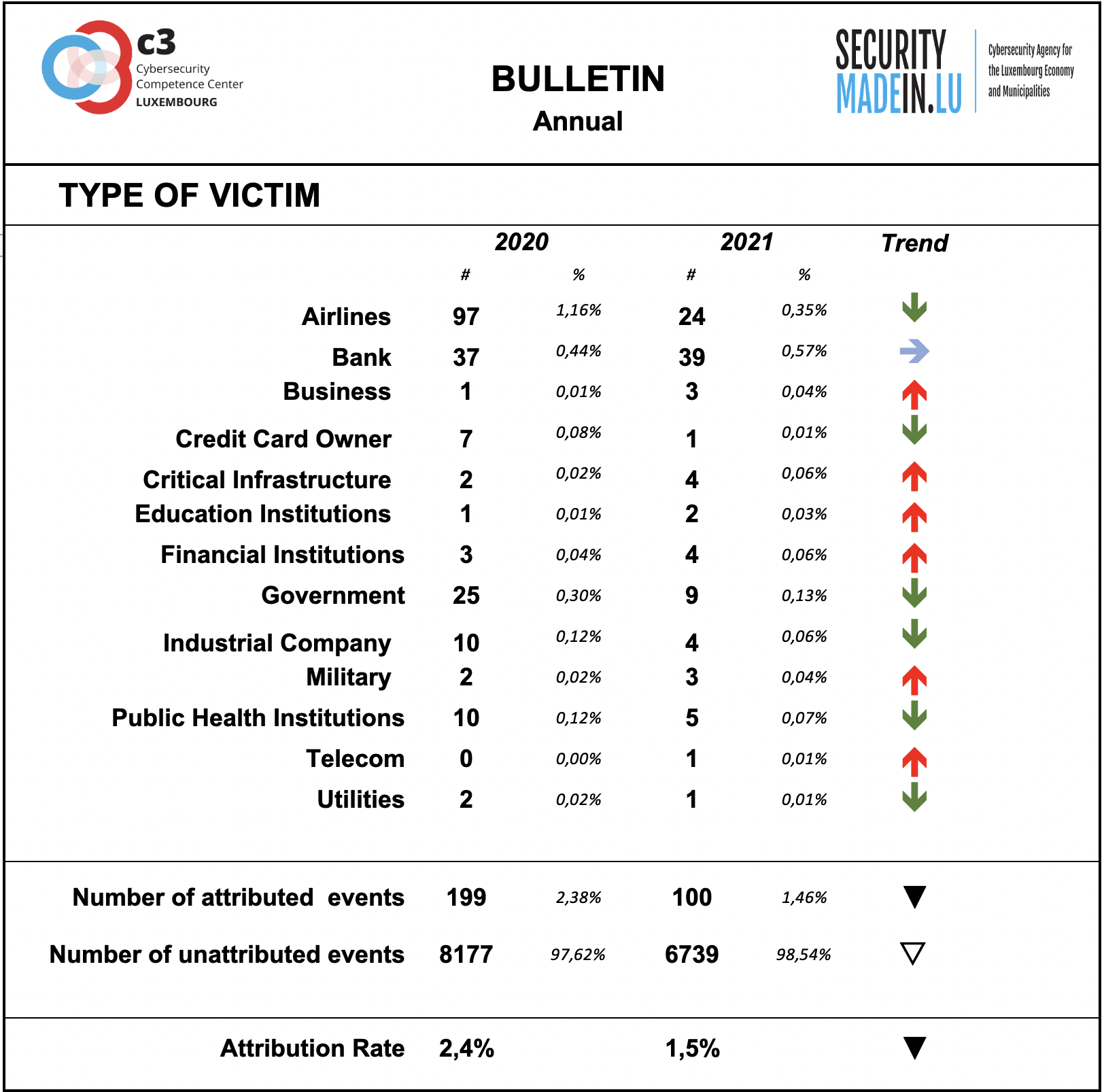
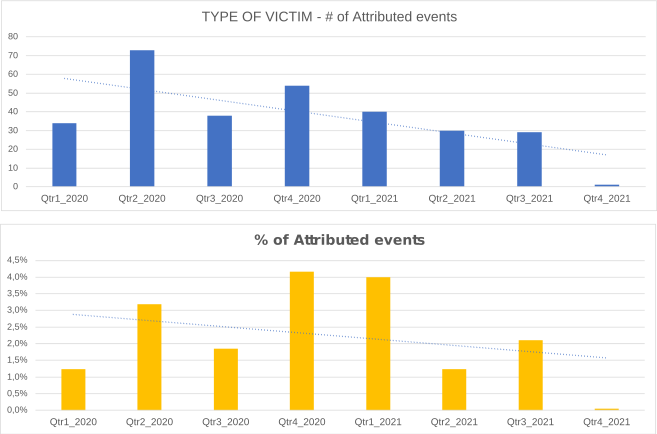
Type of Victim
During 2021 the monitoring system recorded a significant decrease in the exposure of airlines and public utilities. Attacks on banks, critical infrastructures and financial institution are still in evidence.